Discover how AI, blockchain, and smart contracts are transforming cybersecurity by automating compliance and enhancing threat response in real-time.
The increasing complexity of cybersecurity and the rapid evolution of threats demand dynamic and efficient responses. Organizations today are overwhelmed with compliance regulations and cybersecurity policies, often resulting in vulnerabilities due to human error or manual oversight. In the research paper titled “Automated Cybersecurity Compliance and Threat Response Using AI, Blockchain & Smart Contracts” by Lampis Alevizos and Vinh Thong Ta, the authors propose an innovative solution to address this challenge. They present a framework integrating artificial intelligence (AI), blockchain technology, and smart contracts to automate cybersecurity compliance and enhance threat response. Published in September of 2024, this paper outlines a system that aims to reduce manual effort, increase accuracy, and provide real-time adaptability to emerging cyber threats.
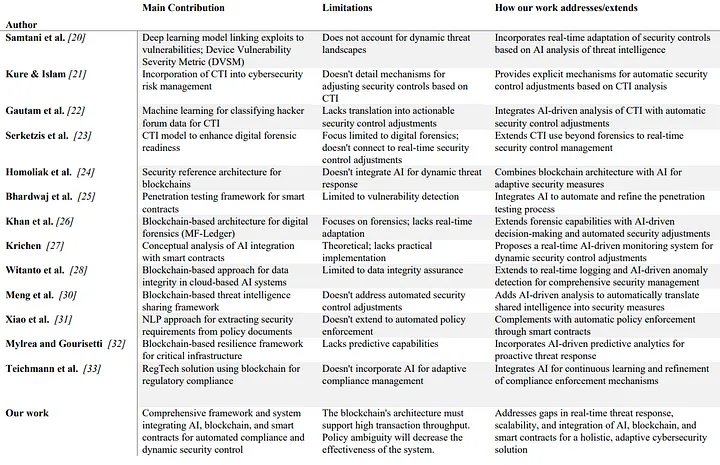
Summary of the Research Article
The central focus of the research is to develop a system that automates cybersecurity policy enforcement and threat response. The key components of this system are AI, blockchain, and smart contracts, each contributing a specific function:
-
AI: The role of AI in the framework is to analyze real-time cyber threat intelligence (CTI), detect anomalies, and dynamically adjust security controls based on the evolving threat landscape. It reduces reliance on manual monitoring and enables quicker responses.
-
Blockchain: Blockchain provides an immutable ledger that ensures transparency and security by recording all compliance and threat response actions. This ledger increases accountability and offers a clear audit trail.
-
Smart Contracts: Acting as automated enforcers, smart contracts ensure that internal cybersecurity policies are followed consistently. They trigger predefined actions in response to AI-detected threats, removing the need for human intervention in real-time security adjustments.
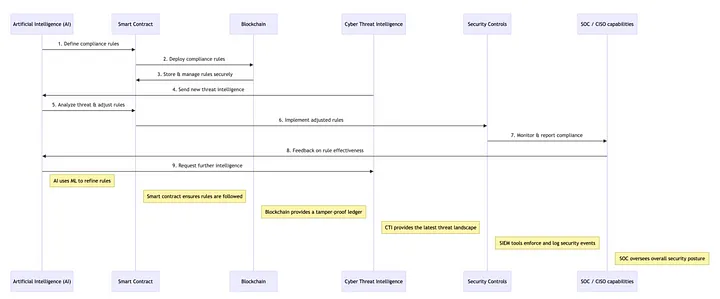
The research methodology includes detailed simulations of the system’s performance in real-world scenarios. By automating compliance tasks that would traditionally be done manually, the system significantly reduces human error and administrative overhead. The paper emphasizes the system’s scalability and effectiveness, showcasing its ability to adapt quickly to new cyber threats.
Critical Analysis
One of the greatest strengths of this research lies in its integration of cutting-edge technologies to solve a critical issue in cybersecurity. The use of AI for real-time threat analysis and blockchain for maintaining an immutable record of compliance actions offers an elegant solution to the challenges of manual security monitoring. Additionally, smart contracts ensure consistent policy enforcement, which is particularly important in industries where even small lapses in compliance can lead to significant security breaches.
However, the implementation of this system is not without potential challenges. For one, the reliability of AI-driven decision-making depends heavily on the quality of the data it receives. While the paper acknowledges this, it stops short of providing a concrete solution for ensuring data sources remain free from bias or inaccuracies. Additionally, blockchain’s scalability issues, such as transaction throughput and storage requirements, are discussed only briefly, even though they could pose significant obstacles in larger organizations with extensive cybersecurity needs.
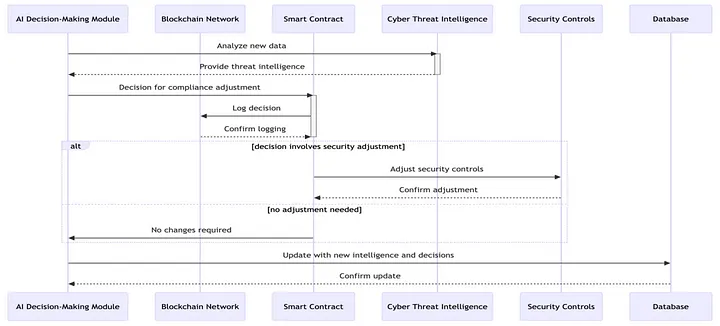
The paper is highly original, building on existing research that uses AI and blockchain for cybersecurity but introducing the novel element of automating compliance via smart contracts. Compared to traditional compliance methods, which require extensive manual monitoring and enforcement, this framework offers a more proactive and efficient approach.
Highlight: The Most Surprising Aspect
One of the most surprising and intriguing aspects of this research is the concept of a self-healing cybersecurity system. The authors propose that by integrating AI with blockchain and smart contracts, the system can autonomously adapt and improve its responses to cyber threats over time. This dynamic, self-adjusting mechanism marks a significant shift from the traditionally reactive nature of cybersecurity to a more proactive stance, which could drastically reduce the time between threat detection and response. The notion that a cybersecurity framework could “heal” itself in real-time by adjusting controls without human intervention is both fascinating and a promising glimpse into the future of cybersecurity.
Implications and Potential
The potential implications of this research are vast, particularly for industries with high compliance demands, such as finance, healthcare, and government sectors. Automating cybersecurity compliance is a game-changer, offering organizations significant cost savings and enhanced security. Moreover, using blockchain to record all actions related to security and compliance can strengthen trust and transparency, crucial elements for organizations working under strict regulatory environments.
Looking forward, this framework opens up several avenues for future research. One possible direction is to explore how the system can be adapted to accommodate external regulatory requirements, thereby making it suitable for global application. Additionally, further work could be done to integrate the system with other emerging technologies, such as quantum computing, to strengthen encryption standards and improve overall security.
Practical applications of this framework extend beyond mere compliance. For example, organizations could use this system to implement real-time threat mitigation, drastically reducing the window of opportunity for attackers. This shift towards automation and proactive defense could revolutionize the field of cybersecurity, making self-adjusting, self-healing systems the norm.
Conclusion
This research presents a compelling vision for the future of cybersecurity — one where manual compliance and threat response tasks are automated through a combination of AI, blockchain, and smart contracts. This system streamlines operations and bolsters security by minimizing human involvement. While challenges remain, particularly around the scalability of blockchain and the reliability of AI, the proposed framework can potentially transform how organizations approach cybersecurity compliance. For anyone interested in cutting-edge developments in this field, this paper is a must-read.
Explore Next
Improve Ethereum Fraud Detection by 20% with AI and Graph Learning
Discover how blockchain is transforming industries on the Blockchain Insights Hub. Follow me on Twitter for real-time updates on the intersection of blockchain and cybersecurity. Subscribe now to get my exclusive report on the top blockchain security threats of 2024. Dive deeper into my blockchain insights on Medium.



评论 (0)