Abstract This talk, presented at EthPrague 2025, introduces "Proof-of-Habitat," a conceptual decentralized protocol designed to address the limitations of centralized data models in smart cities, mapping systems, and environmental protection. By utilizing RF fingerprinting through mobile sensors, Wi-Fi hotspots, and Bluetooth beacons, Proof-of-Habitat aims to validate unique locations securely while preserving privacy with zero-knowledge proofs. The concept prioritizes local participation, ecological conservation, and secure data sharing, with potential applications such as anomaly detection in protected areas and community-driven wayfinding. It envisions a scalable framework for fostering sustainable and inclusive digital ecosystems.
Problem Smart Cities, OpenStreetMap, UNESCO World Heritage and Environmental Protection projects often incorporate open, centralized data models and transparency. They can rely on crowd-sourced financing, direct community involvement, sensor-heavy surveillance, and global access to data, where only a small scope may participate and benefit. Additionally, location-based dependencies in mapping software for mobile phones is monopolized by two major providers, with few alternatives. While satellite systems are nation state-aligned and do provide accurate data, mobile phones also rely on radio frequency (RF) fingerprinting through these providers which collects information on nearby mobile users, cell-towers, bluetooth beacons and wifi hotspots, i.e. wardriving. As ecologies and human-spaces are still tied to locality, a new method of interacting and wayfinding privately through geographic data at scale is needed.
Solution In order to decentralize unique localities, incentivize local-first community-level participation, limit access to infrastructure or user data, and support conservation efforts, I propose a new concept: Proof-of-Habitat. Proof-of-Habitat incorporates RF fingerprinting initially through common mobile device sensors, but can expand to local participation through static Wifi hotspots, bluetooth beacons and ESP32 sensors. Museums have started incorporating bluetooth beacons into city-wide, interactive installations to help tourists navigate sites. Conservationists use combined GPS and RF data to analyze environments in danger. Even private security guards use location-based check-ins via mobile phone to validate patrolling to their employer. Public data in smart cities and conservation efforts can provide a wealth of updated information for academia and engineers in their research and design, reducing the need for travel during the planning phases of a project, however, this also means that threat actors can obtain access to a plethora of data related to city and energy infrastructure. Proof-of-Habitat can be used to limit global access, while commercial VPNs help users and threat actors alike spoof their locations, IP addresses are not enough to validate a person’s location and relevance for a project.
For the Web3 community, Proof-of-Habitat provides a passive sensor-based validation of a person’s or object’s unique location as opposed to Proof-of-Attendance “POAPs”, requiring a human oracle, and KYC-focused Proof-of-Humanity. Furthermore, Proof-of-Habitat can be stored locally on a device, just like an IP routing table, and protected via zero-knowledge proofing, as the agent may determine certain waypoints to mint or offline maps to download during travel. Proof-of-Habit can be commoditized, where one user may provide a proof of a location to another, in much the same way e-Residency models for local brokers and legal representatives are contracted for non-local services from expatriates. Additionally, governance from smart contracting can use Proof-of-Habit to prioritize local-first interactions, essential for any DIY smart home development.
For environment conservation, meshed sensors can be placed around protected locations to collect RF fingerprint over time, determine a baseline, and alert for anomalies. The widely-used current practical use for RF fingerprinting has been in vehicle traffic monitoring and location services, where passing cars with mobile phones cause high fluctuations in an RF spectrum, albeit temporarily, helping to determine travel time. A UNESCO site or National Park sensor might detect unusual increase in human activity and alert the community or ranger. RF scanning is extensively used in war zones for detection of radio-controlled weapons or communications, including for signal-jamming. Smart cities and location-data will increasingly be leveraged in warfighting, hence the concept of “wardriving”. Proof-of-Habitat would eliminate large-scale wardriving efforts by enabling time-based locality validation, limiting data access to temporary visitors. Proof-of-Habitat could help to establish local-only blockchains depending on available storage, i.e. a local cafe router with attached storage may securely store a municipality’s blockchain with Proof-of-Habitat, but a federal government 3000 miles away would not.
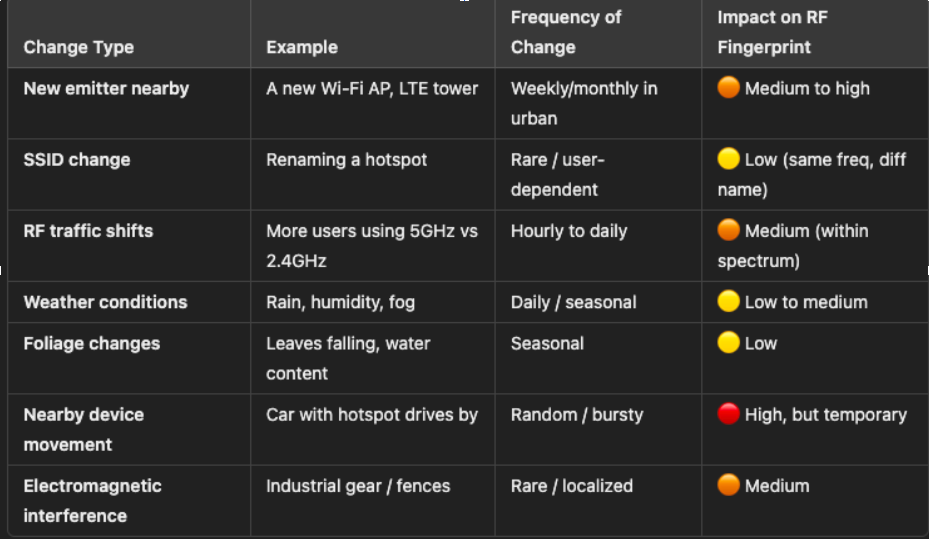
-
The Relativity of Habitat Surroundings
Traditional security mechanisms often rely on static, centralized verification methods that assume a fixed perspective of identity or property. However, in the natural world, ecosystems function as relative, interdependent networks where the value and integrity of a habitat are not defined by human-centric ownership but rather by the continuous interactions of lifeforms within it. Mobile phone operators and ISPs capture similar location relativity through triangulation of cell-towers. I propose that Proof-of-Habitat should reflect this relativity of surroundings, ensuring that no single entity—human, AI, or corporation—can dictate the fate of a region without cryptographically verifiable environmental consensus. By framing habitats as self-validating entities, this system treats violations (e.g. deforestation, poaching, unprovoked human harm) as network disruptions requiring decentralized resolution. A malicious entity may try to change the course of a river in a short period of time (unlike benign beavers), which is detectable downstream and promptly requires a consensus of all those living along the river to mitigate.
1.1 Habitat Verification via Zero-Knowledge Proofs
Rather than relying on explicit human intervention, PoH uses ZK Proof-of-Life (ZK-PoL) to allow living entities to prove their presence within a habitat without revealing unnecessary details. This prevents identity-based discrimination and supports both human and non-human verification: Biological telemetry sensors monitor habitat conditions without exposing individuals Encrypted, periodic peer-sourced measures validate that a habitat remains intact over time ML environmental modeling assesses deviations from expected biodiversity baselines By incorporating zero-knowledge proofing, PoH resists the encroachment of mass surveillance, ensuring that ecological monitoring serves preservation goals rather than oppressive control.
-
Resilience and Incentive Mechanisms
Resilience is fundamental to both ecological stability and decentralized networks. PoH enforces environmental resilience through automated deterrents, distributed verification models, and adaptive incentives.
2.1 Automated Bounty Protocols for Ecological Stability
A major deterrent against ecological harm could be the implementation of eco-bounties—smart contracts that automatically deploy countermeasures against entities that disrupt a habitat. These include: On-chain stake slashing for corporate offenders who violate PoH-protected areas Autonomous drone deployment upon detection of illegal habitat disruptions Real-time economic sanctions via DeFi penalties and asset freezes Decentralized witness incentives, where verified individuals receive rewards for reporting changes in environment
2**.2 Zero-Knowledge Proof-of-Life vs. Proof-of-Humanity**
Unlike Proof-of-Humanity models that focus on biometric KYC verification, Proof-of-Life and proximity to surroundings recognize that:
-
Not all protected entities are human (e.g., endangered species, AI-driven monitoring systems).
-
Anonymity must be preserved to prevent adversarial misuse of KYC data.
-
Attackers should not be able to identify vulnerable targets via public registries.
By leveraging ZK-PoL, any sentient or ecosystem-dependent entity can prove their existence within a habitat while preventing adversarial tracking and the dangers of a surveillance state. The Proof-of-Life protocol could store periodic biometric benchmarks, i.e. active heartrate, as a kind of Deadman’s Switch in the future.
-
-
Infrastructure Considerations
A functional Proof-of-Habitat network requires a mesh-based infrastructure that is resilient to censorship, attacks, and environmental disruptions. This includes:
3.1 Decentralized Habitat Monitoring Nodes
To ensure ecosystem integrity, PoH leverages low-power, autonomous sensor nodes that:
-
Use RF mesh networking (LoRaWAN) for long-range, low-power communication
-
Employ acoustic water-based signaling in aquatic environments to mitigate EMI interference. Extremely useful in the event someone’s cutting your internet cable
-
Maintain blockchain-based immutable logs for cryptographic evidence
-
Distribute data to decentralized storage networks (Arweave, IPFS) to prevent manipulation
3.2 Distributed Proof-of-Habitat Guardians
To prevent human-free zones from becoming attack vectors, a Pokémon Go-style warden system is proposed:
-
KYC-verified individuals validate PoH sensor integrity
-
Warden staking mechanisms ensure non-biased environmental reporting
-
AI-enhanced anomaly detection prevents collusion and fraud (double bounty hunting)
-
-
Coordination and Governance
PoH operates as a self-sustaining decentralized governance system through:
-
DAO consensus mechanisms, where nodes can verify environmental integrity without revealing raw data
-
A Quadratic Funding for Eco-Defense, where individuals can collectively finance habitat preservation, fulfilling William James 1910 “Moral Equivalent of War”
-
Digital Potlatch, where lands or digital assets are automatically reassigned in the event of illegal habitat destruction, a mechanism for autonomous resource reallocation
-
A layered Multi-Species Protection Model, ensuring that protection extends to all forms of verified life rather than just humans or economic interests
-
-
Ethical and Political Implications
The transition from Proof-of-Humanity to Proof-of-Habitat poses significant philosophical and governance challenges:
-
Do non-human entities deserve cryptographic representation?
-
Can AI or embodied superintelligence claim ecological rights?
-
What are the thresholds for defining "habitat destruction"?
-
How do decentralized eco-bounties remain accountable?
A decentralized Proof-of-Habitat model forces us to reconsider these questions within an interoperable, politically-neutral cryptographic framework that is resistant to centralized manipulation while maintaining ecosystem autonomy.
-
-
Conclusion
Proof-of-Habitat represents a paradigm shift in decentralized identity, cryptographic security, and ecological governance. By enforcing deterrence through relative environmental validation, resilience incentives, eco-bounties, and ZK-Proof-of-Life, we propose an autonomous, decentralized protocol that protects not just individuals, but entire ecosystems from collapse.
As we transition toward a world where AI, bio-integrated sensors, and blockchain-based governance systems interact with human and non-human actors alike, Proof-of-Habitat serves as a foundational protocol for defining and defending the autonomy of natural and synthetic life.
Actionable Next Steps
-
Testnet implementation of PoH with ZK-biodiversity proofs
-
An eco-bounty DAO to fund deterrent mechanisms
-
A multi-species environmental governance framework
-




评论 (0)