Introduction
This article is intended as an informative exploration of the mechanisms and infrastructure that power our online experiences. During this journey, we'll navigate through the intricate web of protocols and processes that seamlessly connect us to the digital world. We're going to take a closer look at how the internet works behind the scenes to keep our communication flowing smoothly between devices and networks. Along the way, we'll use simple stories and comparisons to explain tricky ideas and make the technical stuff easier to understand. I also dedicate a large part to privacy and security aspects on the internet which I consider part of the fundamental rights.
From establishing connections through IP addresses to unraveling the role of the Domain Name System, the exploration delves into the fundamental aspects of internet navigation. Highlighting the significance of protocols in standardising global communication, we delve into the crucial role of security protocols and cryptography in safeguarding data transmissions. With a steadfast focus on privacy and security, our expedition scrutinises challenges posed by censorship. The journey concludes with some mitigation strategies that can be adopted to remain anonymity and avoid censorship.
1.The internet Journey
1.1 IP addresses
The journey starts with establishing a connection to the internet. A pre-requisite for any device (be it a phone, computer, IoT device…) designed to connect to the internet is for it to be equipped with a network card and get an IP address assigned. The network interface card (NIC) is built in the hardware of your device and contains a Media Access Control (MAC) address that will enable it to communicate with routers. This MAC address (also called device ID) will allow the router to distinguish the devices connected to it.
There are three different ways for your device to connect to the internet: via Wi-Fi, via an ethernet cable, or via your phone’s mobile/satellite network. The first two involve connecting to a router, while the latter communicates with cell towers or satellites operated by your phone provider to access the internet. One important job of the router is to give devices an IP address when they connect through Dynamic Host Configuration Protocol (DHCP). There are also static IP addresses, but they're not as common now because they can cause security issues.
The MAC address stays the same on your device, but its IP address can change. When you disconnect from the router, your IP address goes back into a pool. When you connect again, you might get the same IP or a new one. Your IP address depends on the network you're using. So, if you switch from home Wi-Fi to a restaurant's Wi-Fi, the restaurant's router gives you a new IP. This also happens if you use wired or cellular connections, as each network type has its own IP assignment.
1.1.1 Public vs Private IP addresses
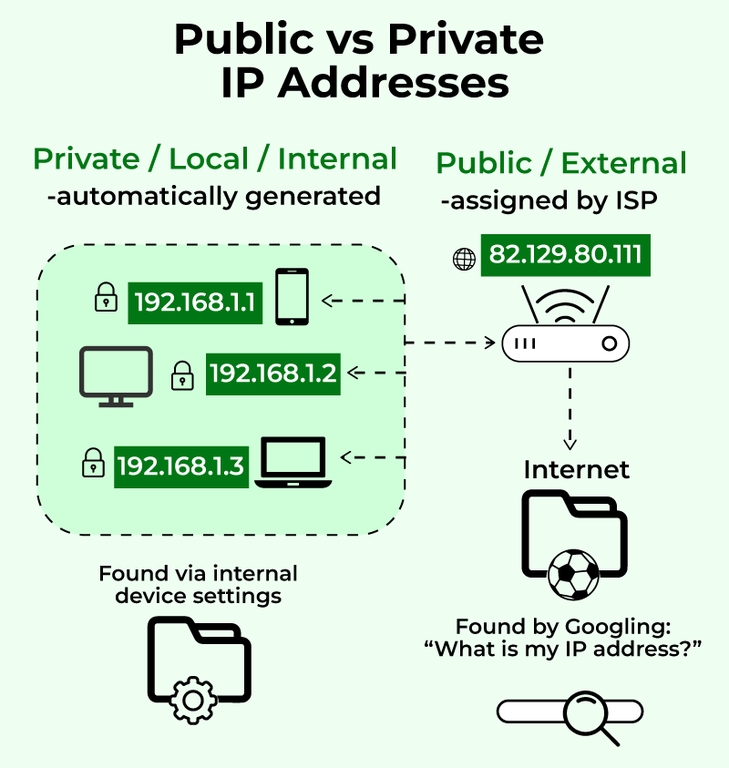
When connecting to the internet, understanding the difference between public and private IP addresses is crucial. While they both serve as unique identifiers for your devices, their roles and scopes differ significantly.
Private IP Addresses: Hidden Network Heroes Most connections, whether through Wi-Fi or ethernet cables, utilise private IP addresses. These addresses, assigned by your router, act as internal identifiers within your local network, like your home or office. Think of them as apartment numbers within a building – unique for each resident but unknown to the wider world. This ensures efficient resource allocation within your network and maintains security, as devices outside cannot directly communicate with them.
Public IP Addresses: Stepping Out onto the Internet In contrast, public IP addresses serve as your network's gateway to the vast internet. Assigned by your internet service provider (ISP), they act as your building's address, visible and recognisable to the online world. When you browse websites, stream videos, or connect to online services, your public IP address allows you to participate in the global digital landscape.
Cellular Networks, unlike Wi-Fi or wired connections, don't involve routers. Instead, cell towers relay signals to your mobile network operator (MNO). The MNO assigns a temporary public IP address unique to your device, enabling direct communication with the internet without a router. However, this address changes as you move between cell towers, ensuring network efficiency and resource management. Wi-Fi and Wired Networks: Devices connected through Wi-Fi or ethernet cables receive private IP addresses from your router. These addresses are unique within your local network but not visible on the broader internet. Think of them as individual mailbox numbers within the apartment building; they allow the router to deliver incoming data from the internet (the mail) to the correct device. It's crucial to note that devices on the same Wi-Fi network cannot directly communicate with each other – all communication must flow through the router, acting as the central mailroom.
1.1.2 Data transmission over Wi-Fi connection
Here follows how a data transmission would have happened in practice over a wifi connection with dynamic protocol:
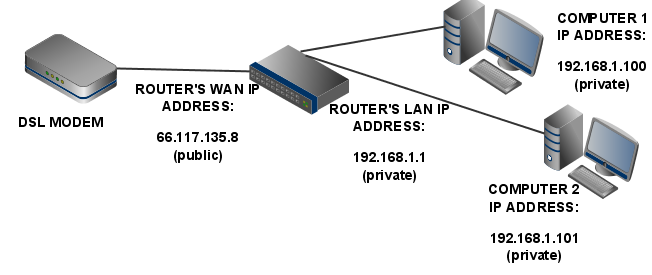
The web service delivers the data to the router (which has a public IP address) which will deliver the data to your device that has the private IP address.
Routers are special because they have two IP addresses:
-The first router interface is called the WAN (Wide Area Network) interface. This is the side of the router that faces the Internet and has a public IP address.
-The second router interface is called the LAN (Local Area Network) interface. This is the side of the router that faces the home network’s computers and has a private IP address.
1.1.3 IP address formats
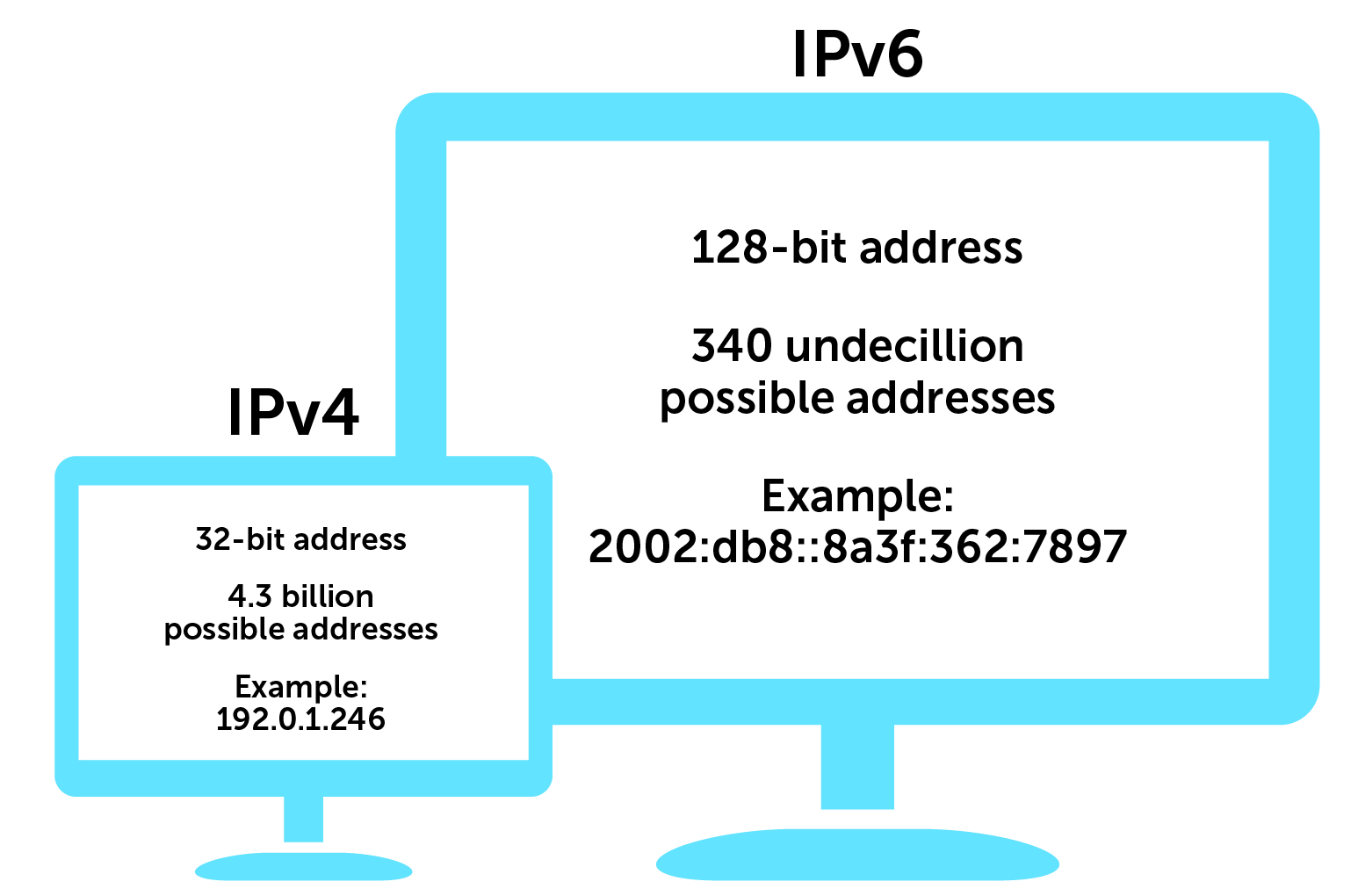
Each IP address is unique and will have a specific format. There are two different generations of IP addresses and formats: IPv4 (32-bit address) and IPv6 (128-bit address). IPv6 was enacted as the total number of unique addresses that could be created with IPv4 was a ‘mere’ 4,3 billion. The newer IPV6 format will allow more than 340 undecillion possible addresses. Besides this, Pv6 will also enable your device to be reachable from the outside world - thus publicly reachable and able to provide services as well as actively participate in the internet. More information about this here. Most routers nowadays are IPv6 enabled and will thus assign your devices IPv6 addresses next to an IPv4 address. If you are curious to know which IP address(es) your router has assigned to your device you can easily verify that in the setting of your device. Note that most people’s router and device will have both an IPv4 address and IPv6 addresses. The former is necessary for accessing all websites today. The latter is more for the future as websites eventually transition to the newer IPv6 naming convention - how long that might take is anyone’s guess though. That is because you need a device with an IPv6 address to access a website that only has an IPv6 address (as websites can have both IPv4 and IPv6 addresses). IPv4 and IPv6 are different protocols and function entirely independently and cannot communicate with each other directly. A device with an IPv4 address cannot "speak" to a device with an IPv6 address. Which IP address number you receive depends on your router, Internet Service Provider (ISP) and region.
Once our device has one (or multiple) IP address(es) assigned, the router (with its private and public IP address) will act as the entrance to the rest of the internet and allow us to communicate with other nodes and IP addresses in the network.
1.2 DNS & URLs
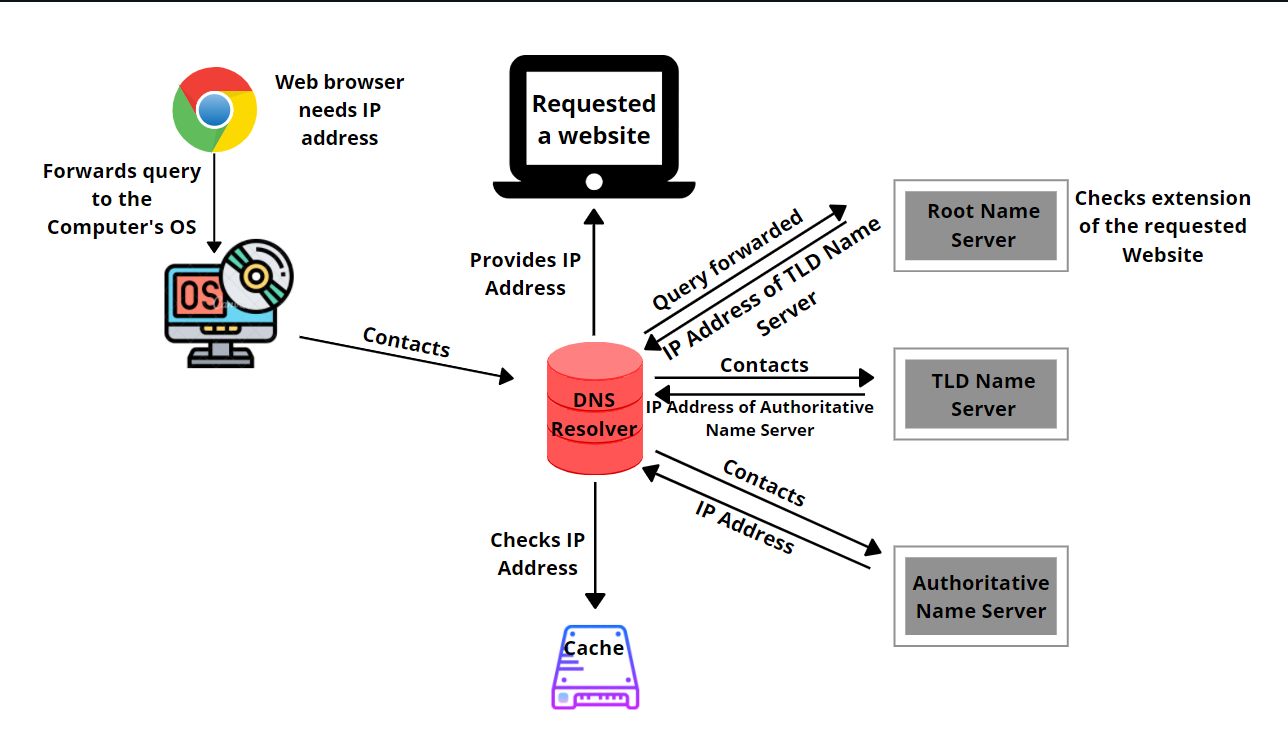
Just as our devices and routers are identified by IP addresses, the online services we use, such as mail servers, apps, and websites, also have their own IP addresses. These services can be accessed by querying their IP addresses and getting a response, enabling communication between our devices and the servers hosting these services. To access a particular website, such as Wikipedia, your browser needs to know its IP address. While manually entering these lengthy and complex IP addresses would be impractical, as they are hard to remember and may be easily confused with each other, we rely on the Domain Name System (DNS) for convenience. DNS is a public and decentralised database that links a name to an IP address, this is why we sometimes call it the telephone book. It is public as everyone can have access to it, and it is decentralised as this ledger is kept on hundreds of different servers around the world. The goal of such a set-up is to increase the resiliency of the network in case one of the servers goes down – so that in this case another DNS server will meet our request and retrieve the IP address of our online service we wish to access.
If you are curious and want to lookup the IP address of your favourite website you can do that in various ways including using the computer terminal or an online DNS resolver.
So in short, when entering the url wikipedia.org in our browser, it will request a DNS to resolve this to an IP address. Once the IP address is found by a DNS resolver it will send it back to the browser and ensure the connection to the site. The first time we make a DNS request, our browser, computer or ISP often saves or caches this info for future requests. By default ISPs will run DNS servers for their clients. When assigning an IP address to your device, your router is also sending the address of the DNS resolver. If that DNS resolver can’t find the IP address of the queried service it will ask the server higher up and so forth.
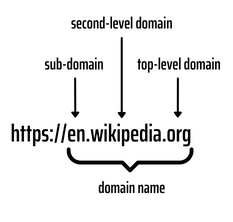
Looking at the URL of en.wikipedia.org as an example, we can decompose it into different parts. The very first part (en) is a sub-domain (which is optional and does not always exist). The part after that is called a domain name and the last part is a top-level domain (TLD).
The TLDs can be split up into generic top-level domains (gTLD) and country code top-level domains (ccTLD). There are about 290 ccTLDs and 1200 gTLDs. The actor overseeing TLDs is the ICANN. For more info on DNS and URLs.
1.3 Web Browsing - HTTP(S)
Once DNS resolves the IP address based on the domain name entered in the URL, the next step involves HTTP or HTTPS protocols facilitating the transmission of data to that IP address. You might remember these acronyms form the first part of the URL in old browsers. HTTP stands for Hypertext Transfer Protocol. This protocol dictate how information is exchanged between your device and the web server, forming the backbone of our online interactions. Technically, it will control how hypertext is exchanged and transmitted.
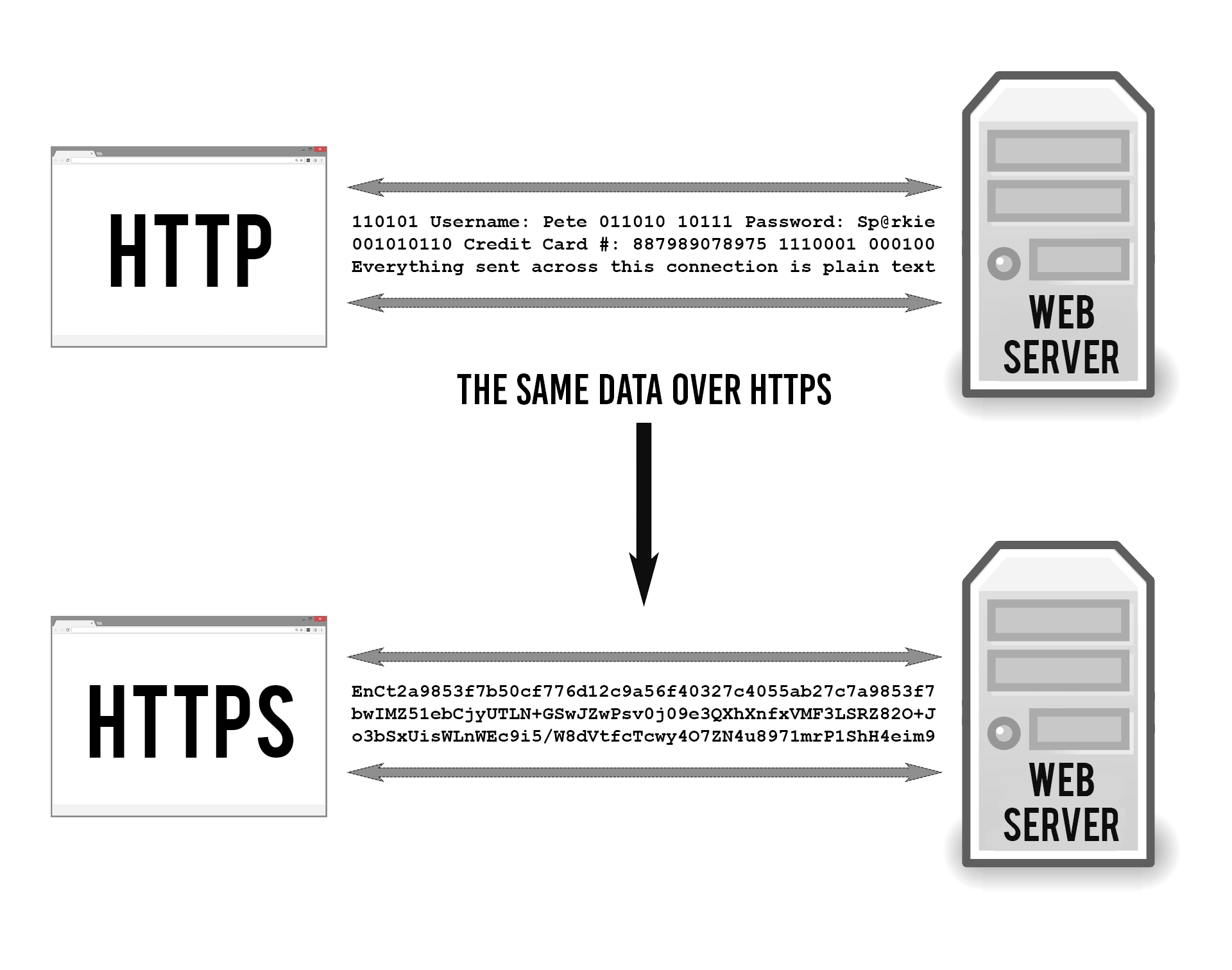
The difference between HTTP and HTTPS, is that the former is not privacy sensitive as routers (and other intermediate devices) can read and modify your data transmitted over http. This is far from ideal and thus why https came into being. HTTP(S) will encrypt the message body and header, before it is sent over the network. The only part which is not encrypted is the IP address as it must know which destination web server it needs to return the data from. So, when you send data over an https connection, the information is encrypted before its transmission and decrypted only by the intended recipient (the web server). This encryption prevents intermediaries (such as network routers or potential attackers) from reading the actual content of the data. Additionally, the security stems from a handshake process which guarantees data integrity. HTTPS stands for HTTP + TLS (transport layer security). Whichever protocol (HTTP or HTTPS) is used, is not up to you but up to the service providing the resource and content to decide. The destination web server (wikipedia for example) will thus determine if they’re able to provide their clients with a secure connection.
So whenever you want to access a service on the web, an HTTP(S) request message will be submitted to the server. That HTTP(S) request is constructed of both the header (requested resource, browser info etc) and the body. Once that request reaches the server with the desired content, it will send an HTTP(S) response back, which is again made up of a header (status code, content type) and a body consisting of the requested resource as content. One well- known status code is the 404 one, in case the requested resource could not be found.
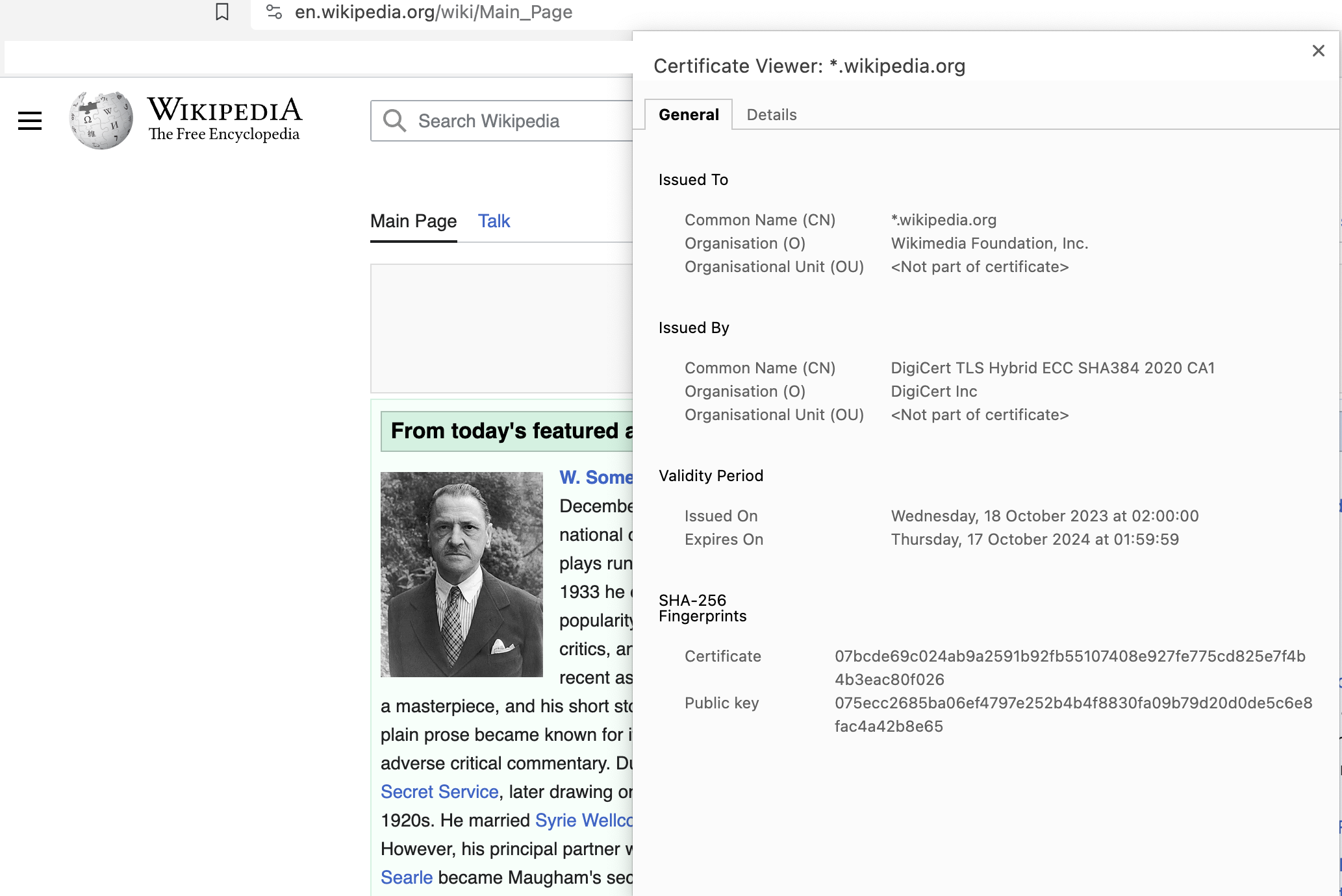
If the URL begins with HTTPS (and not HTTP), it means the site is secured using a TSL certificate. Most browsers don’t display this in the url anymore, but you can check the site information. This is usually a button before the url bar where security info can be retrieved and we can check if the connection is secure as well as verify the TSL certificate details. As a side note, TSL is the successor of SSL (Secure Sockets Layer). The certificate authorities (CA) will issue the digital certificate to service operators which attest to ownership of the operator’s key. The certificate contains information about the certificate owner, issuer and validity period, as well as a copy of the public key and cryptographic signature of the CA.
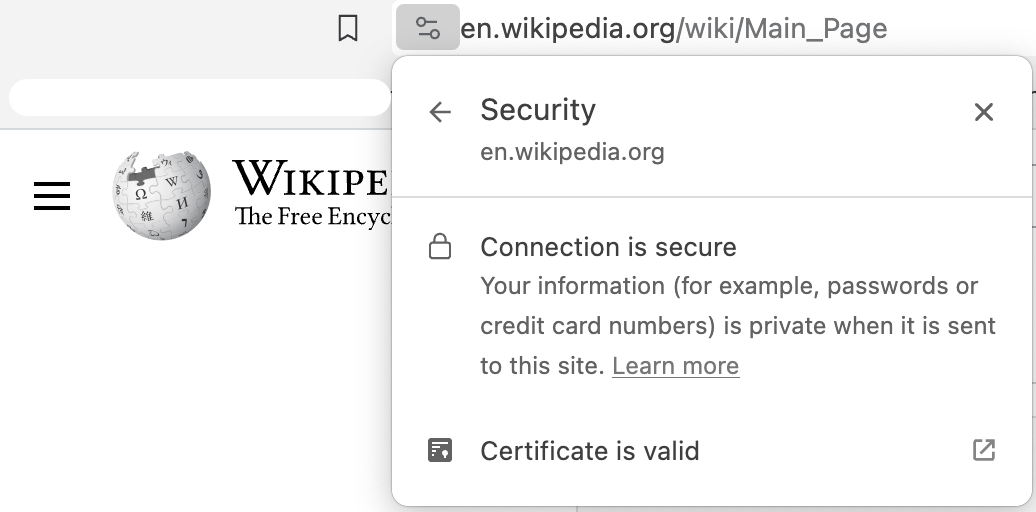
So, is HTTPS enough for complete online anonymity? While HTTPS safeguards the content of your communication by encrypting it within a secure tunnel, it doesn't offer complete anonymity or shield your entire online identity. Here's why:
-
Beyond the tunnel: Techniques like browser fingerprinting analyse your device's unique configuration, including fonts, plugins, and screen resolution, potentially identifying you even with HTTPS.
-
Server-side logging: Websites might still log information about your connection, like your IP address or browsing history, even if the content itself is encrypted.
-
Metadata exposure: Data packets carrying your communication contain metadata, such as sender and recipient addresses and timestamps, which are often not protected by HTTPS and can reveal information about your activities.
-
Pseudonymous, not anonymous: With encryption, you remain at best pseudonymous, meaning your identity can be linked to your online activity even if the specific content is hidden.
-
Unveiling beyond content: Even the information you actively share like your operating system and browser details can contribute to identification. Additionally, visiting web pages coded with advanced technologies like JavaScript (JS) or HTML5 can further expose details like your screen resolution or even remaining battery without your explicit knowledge or consent. Therefore, while HTTPS is crucial for securing communication, it's important to be aware of its limitations and take additional measures for greater anonymity. This might involve using privacy-focused browsers, avoiding websites with excessive tracking practices, and employing tools like TOR or VPNs for anonymising your IP address.
1.4 Data Transmission
1.4.1 Transfer of Data
When you interact with the internet, whether browsing a website, sending a message, or streaming a video, you trigger the transfer of data from your device to the server hosting the required content. This data, fundamentally composed of ones and zeros, travels through the internet in packets - small containers carrying information along with addresses and other details. These packets can be transmitted across various physical mediums like copper wires (electrical signals), radio waves (air), or fiber optic cables (light signals), depending on the infrastructure available. For example, when you send a photo to a friend, the image data is divided into packets, each containing the sender's and receiver's IP addresses, packet type, and size. After passing by the messaging app's servers these packets reach their destination (your friend’s device), where the data within them is interpreted and reassembled to recreate the original image on the recipient's device.
Your device, like your phone or computer, has a unique private IP address within your home network. This address appears in the headers of data packets it sends. These packets first reach your router, the central device coordinating your home network's internet connection. Think of it as your local post office. The router reads the destination address on each packet and forwards it to your internet service provider's (ISP) larger router, which acts like a central sorting facility. From there, additional routers relay the packets based on their addresses until they reach their final destination. To ensure secure and private data transmission, protocols like IPSec can be used. IPSec employs encryption and digital signatures to verify the authenticity and integrity of data packets, guarding against tampering or interception.
1.4.2 Protocols
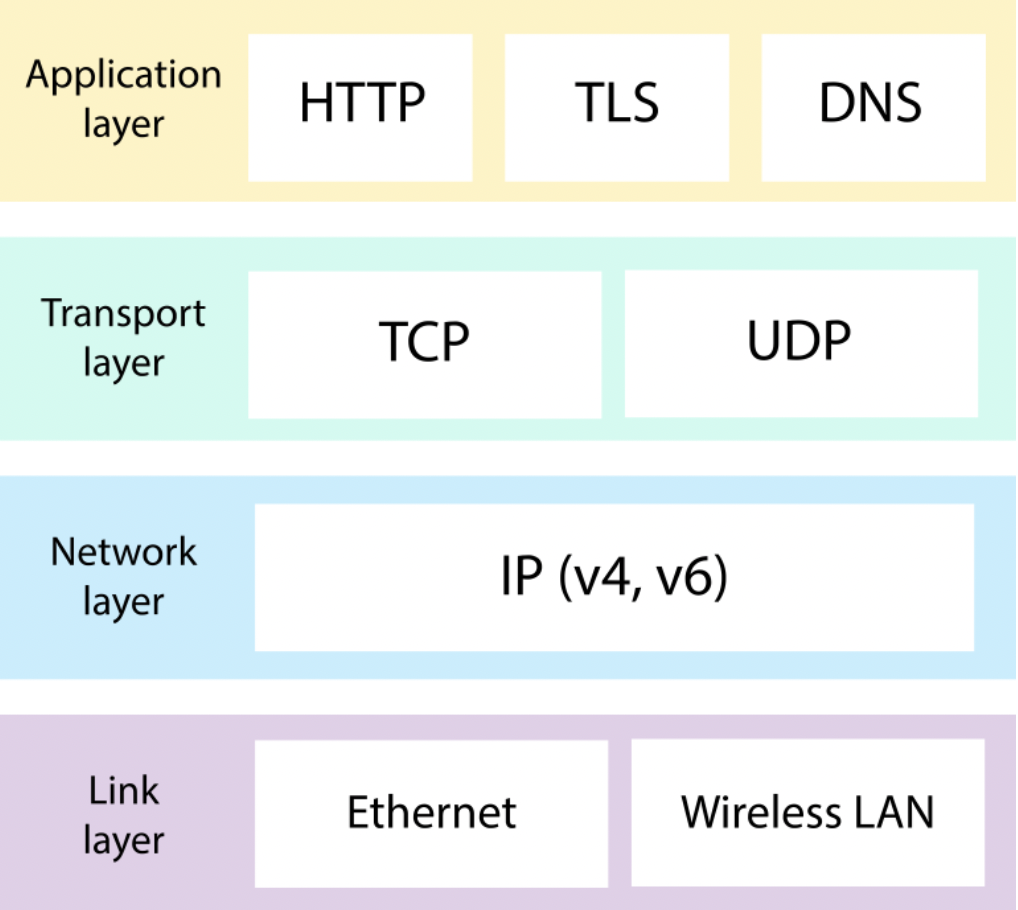
In the vast internet landscape, a multitude of protocols serve as the guiding principles that define how this interconnected web operates. These protocols establish standardised rules, akin to a shared language, facilitating seamless communication and data exchange among the myriad actors and nodes within the network. They form the backbone, providing a structured framework that ensures smooth interactions and prescribes solutions for potential challenges that may arise during the dynamic dance of data transmission. We already discussed 2 protocols previously, namely HTTP and HTTPS that manage how data (hypertext) gets transmitted over the web.
Internet Protocol (IP) This standardises and outlines how packets are structured and how addresses on the internet must be formatted to successfully deliver the packets to their destination. Devices will thus have to be able to speak in ‘Internet Protocol’ (by adhering to its rules) to communicate seamlessly together.
Another set of important rules that govern the internet relates to how to transmit packets from one node to the other. There are two general transport protocols: Transmission Control Protocol (TCP) User Datagram Protocol (UDP) Both protocols will regulate how packets get from the sender to the recipient. In short, TCP will optimise for reliability but at the expense of speed. UDP on the contrary will optimise for speed while being less reliable. Whichever is in use depends on the service that you are using. The UDP protocol is commonly used for video streaming and online gaming. TCP is frequently used by the world wide web, email and p2p applications.
Recently a new transport protocol came onto the scene: Quick UDP Internet Connections (QUIC). It will try to combine best of both worlds by being reliable and fast. It will achieve this by using the UDP protocol in an ingenious way (with QUIC datagram). Those protocols are thus the ones that handle the splitting of data into smaller data packets at the sender’s side, and reassembling them on the receiver’s side.
Border Gateway Protocol (BGP) is the routing standard on the internet and will enable routers to know which direction a packet should be sent to, so that it would arrive to its destination in a cheap and fast way. It can thus be likened to a GPS in some sense. The internet isn’t one unified network but rather a set of smaller connected networks called autonomous systems (AS) (belonging to universities, ISPs and telecommunications companies). These interconnected ASs form the internet as we know it. There are about 97 000 at the moment.
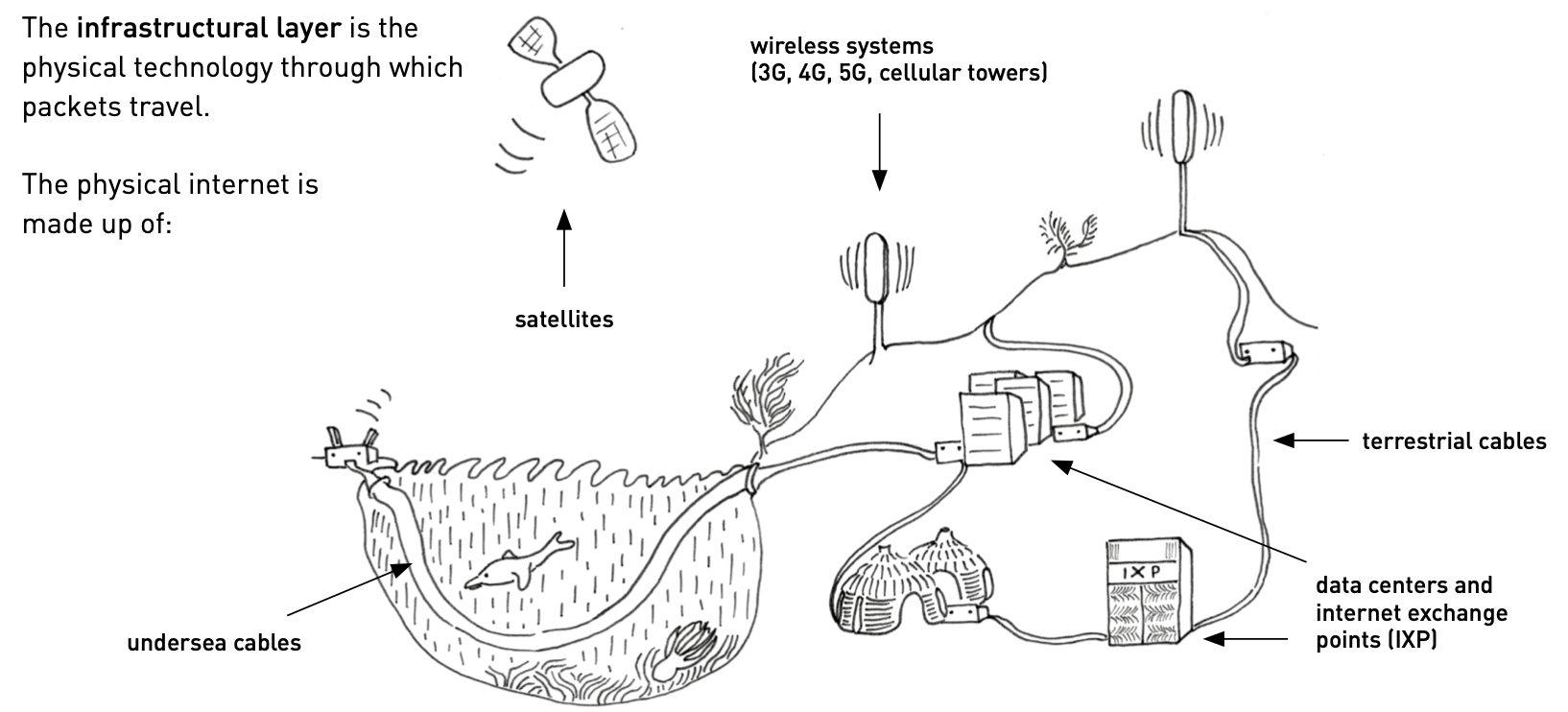
WEP, WPA, WPA2 & WPA3 - Wifi security Protocols
You can access the web interface of your router in the same way you access a website - by entering its IP address in your browser. 192.168.1.1 is the IP address pre-specified by most router companies as the default gateway address and can be used to make different changes to the router’s settings. This web interface will allow you to configure settings such as change WiFi passwords & SSID, check connected devices and remove any undesired or unknown ones, as well as create guest users. This article advocates for setting up a separate network for any guest willing to connect to your router to avoid any risks or issues. One of the things that can also be maintained via the router’s web interface is the security protocol in use.
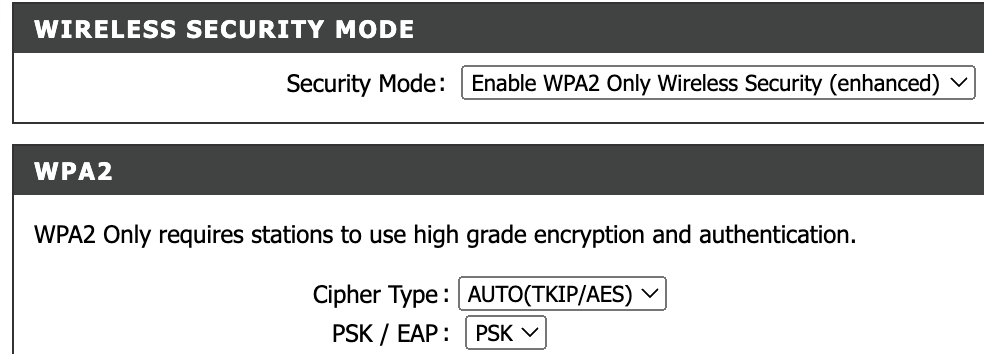
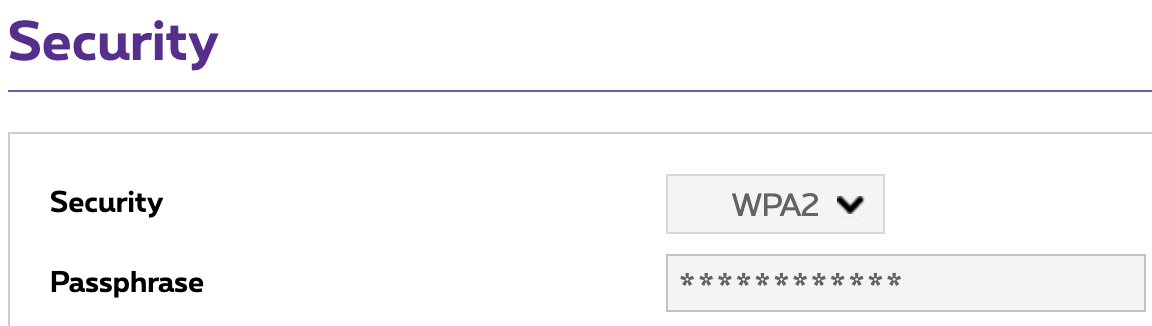
Wireless networks are more vulnerable to cyberattacks compared to wired networks. It is important to secure wireless connections to keep your data hidden and protect your communications, while blocking hackers from your network. If your router is unsecured, someone could access it, use it for illegal activities in your name, track your internet use or install malware. To keep you safe while browsing, some wireless networks have security protocols that encrypt your online data. Your router will usually ship with one of the following security protocols: WEP, WPA, WPA2 and possibly WPA3 - from least to most secure. This website offers a good overview of these protocols and how they function. It is recommended to use WPA2 or WPA3. Make sure to only enable WPA2 as there is an attack surface if your device is WEP compatible. Whichever can be activated depends on your router and the protocols it supports.
2. Putting it all together - From Click to Content
Let's recap the whole journey from click to content (over a Wi-Fi connection with dynamic IP addresses):
-
The Spark: Your Action Initiates the Journey It all starts with your action. Whether you tap a website link, send an email, or stream a video, your device converts that request into data packets, the digital building blocks of information. These packets contain not only the information itself but also crucial addresses – one for the destination (the website server or email recipient) and your own private IP address, acting like your unique apartment number within your home network.
-
Internal Communication: Router Takes the Helm The data packets then embark on a short trip within your home network. Your device sends them wirelessly to your router, the central traffic manager. The router recognises the packets' private IP address, identifying them as originating from your device.
-
Stepping Out: Public IP and the Internet Gateway Next comes the crucial step of connecting to the vast internet. Here, the router plays a double role. It might already have a temporary public IP address assigned by your internet service provider (ISP), acting like your home's address visible to the online world. If not, the router uses DHCP (Dynamic Host Configuration Protocol) to request one from the ISP.
-
Bridging the Gap: Translation and Transmission Now, the magic happens. The router translates your device's private IP address to its own public IP address, essentially putting your home's address on the data packets. It then encapsulates them within new internet-compatible packets and sends them off to the wider world through the WAN (Wide Area Network) interface, your router's connection to the internet.
-
The Grand Expedition: Through the Labyrinth of the Internet Think of the internet as a sprawling network of highways and routers. Each data packet embarks on a unique journey, hopping from router to router based on its destination address. It traverses the internet backbone, a complex web of high-speed connections, until it reaches its final destination – the server hosting the website or service you requested.
-
From Server to You: The Response Arrives The server processes your request, gathers the necessary information (website content, email data, etc.), and packages it into a response data packet. This packet carries the website content or email, along with the router's public IP address as the destination since it originated from your device.
-
Homecoming: Back Through the Internet Maze The response packet retraces its steps, navigating the vast internet infrastructure with the help of countless routers. It finally reaches your router, recognized by its public IP address.
-
Delivery to Your Door: Reaching Your Device Finally, the router uses the private IP address stored within the packet to identify the intended recipient – your device. It delivers the data packet wirelessly, and your device eagerly unwraps it, interpreting the information as the website you requested, the email you were waiting for, or the video you wanted to watch.
This seemingly instantaneous process involves a complex, orchestrated dance of devices, protocols, and infrastructure. By understanding the flow of data and the roles of different players, you gain a deeper appreciation for the magic that happens every time you connect to the internet!
To make it it even more pragmatic and concrete I cover a real-life example below of something that we probably all do on a daily basis: sending a message via WhatsApp or an Email via Outlook.
Imagine you want to send a message to your friend Alice through WhatsApp or email:
-
Crafting Your Message: Both WhatsApp and email begin with your interaction. You type your message, perhaps adding a pictures or attachment. WhatsApp compresses these media for faster delivery, while email might struggle with larger attachments depending on your provider's limits.
-
Encryption and Packaging: This is where the Internet protocol (IP) will come into action and take care of structuring and routing packets effectively. Also the Transmission Control Protocol (TCP) is relied upon to make sure those packets arrive at their destination in one piece. There is some divergence between WhatsApp and email though. The former enables end-to-end encryption by default (which happens through the Signal protocol). Your message and media become an encrypted package, unreadable even by WhatsApp itself. Conversely, email, unless using specific add-ons, transmits data in plain text, potentially accessible to servers along the way.
-
Server Relay and Routing: Both platforms leverage servers to bridge the gap between you and Alice and where the both WhatsApp and email servers act like clever traffic guides, using the Border Gateway Protocol (BGP) to find the fastest route for your message packets. WhatsApp doesn't store your encrypted message, ensuring privacy. Email servers, however, temporarily store your unencrypted message until delivery, raising security concerns.
-
Reaching Alice’s Device: The encrypted data packet in WhatsApp finally lands near Alice’s device. Her phone uses a unique decryption key to unlock the message and media, making it readable. For email, the journey might involve complex server communication if Sarah uses a different provider. Finally, the message arrives in her inbox, ready to be opened.
-
Storage and Retrieval: The story doesn't end with delivery. WhatsApp messages primarily reside on your and Alice’s devices unless explicitly deleted. Backups (Google Drive/iCloud) are optional and don't involve WhatsApp servers directly. In contrast, Outlook.com emails are stored indefinitely on Microsoft servers until deleted or storage limits are reached. While you can download your mailbox locally, it won't automatically update.
As you can see, there are some nuances and key differences between both services:
-
Privacy: WhatsApp's end-to-end encryption offers superior privacy compared to unencrypted email by default.
-
Storage: WhatsApp messages are primarily local, while emails reside on servers, impacting accessibility and potential privacy concerns.
-
Media Handling: WhatsApp efficiently handles smaller media, while email might struggle with larger attachments depending on provider limits.
-
Offline Access: You can access WhatsApp messages offline if stored locally, whereas email access typically requires an internet connection.
Note that we are not using http or https at any point in time as we are not accessing any web pages or communicating with any web servers. Instead they use different protocols to communicate between devices and servers, like Signal Protocol for WhatsApp and SMTP/POP3 for email.
3. Privacy and Censorship
3.1 Cryptography
We've just witnessed the fascinating journey of your data, traversing networks and protocols to reach its destination. But technology's power to connect comes hand-in-hand with complex questions of privacy and censorship. This chapter delves into these cornerstones of internet values, exploring the delicate balance between the freedom to communicate and the protection of our digital footprints. While we briefly touched upon protocols like encryption securing our online journey, their limitations become evident when navigating the vast digital landscape. The fight for privacy requires a deeper understanding of the forces at play, and cryptography emerges as a pivotal guardian in this battle.
Pervasively utilised in security protocols like HTTPS, TLS, and WPA2, cryptography employs two fundamental techniques: signing and encryption.
Ensuring Authenticity: Signing Data
Imagine you're sending a letter, and you want to make sure the recipient knows it's really from you. So, you add a unique signature at the end. In the digital world, this is like putting a digital fingerprint on your message to prove it's genuine. When the recipient gets your letter, they can check this digital signature to confirm it's truly from you and hasn't been tampered with during delivery.
Furthermore, I foresee that these cryptographic signatures will gain importance and adoption with the rise of deepfakes and AI-generated videos.
Transforming for Security: Encryption
Now, let's say you want to send a secret message, but you're worried someone might try to sneak a peek. Encryption is like turning your message into a secret code that only you and the intended recipient can understand. It's a bit like writing a secret note in a made-up language. You both have a special key to decode the message, making sure no one else can figure it out.
Safeguarding Transmission: Transport Encryption
When you're surfing the internet, your data is like a letter traveling through different post offices. To keep it safe, websites often use a special security system called TLS. It's like sending your letter in a super-secure envelope that only the recipient can open. However, sometimes there might be fake envelopes or situations where the whole delivery route isn't entirely secure.
But our online presence extends beyond messages in transit. The information we store on devices and servers also requires protection. Here, an additional layer of encryption comes into play: Data at Rest Encryption to secure stored information.
Now, imagine your messages or files sitting on your computer or a server like pictures stored in a cloud.
Data at rest encryption is like putting these files in a magic box that only opens with a secret key, say a password. Even if someone manages to grab the box, he won't be able to see what's inside without the right key.
So, in simple terms and using analogies, signing data will enable a unique stamp on your message, encryption is turning it into a secret code, transport encryption is like sending it in a super-secure envelope, and data at rest encryption is keeping your files safe in a magic box that only you can open. Together, these methods help keep your online communication safe and sound.
Moreover, cryptography may be poised to disrupt another realm: passwords. Imagine logging in to websites without remembering complex combinations, but simply using your fingerprint or a secure device like a phone. This is the promise of passkeys, a novel approach leveraging cryptography. Instead of static passwords, passkeys utilise unique pairings of public and private keys, stored securely on your device. Websites hold the public key, and your device uses the private key, like a digital signature, to verify your identity during login. No more password sharing or phishing worries, all thanks to the power of cryptography!
3.2 Internet Censorship
As detailed previously, the internet is a vast, interconnected network spanning the globe. When data packets traverse this network, they encounter numerous potential points of censorship that can disrupt internet connectivity. One aspect of the internet I care deeply about is the principle of network neutrality which emphasises that networks should treat all data packets equally, regardless of their content, ensuring an unbiased approach to data transmission. However, various entities (like governments, institutions or telecommunications companies) may seek to control or restrict access to internet content, leading to censorship.
Censorship manifests at various layers of the internet protocol stack:
-
Physical Layer: Disruptions to physical infrastructure, such as damaged or severed cables, can disrupt connectivity and restrict access to online content. Whether resulting from malicious actions like Russia targeting critical internet infrastructure in Ukraine, or accidents, such disruptions can have significant impacts.
-
Network Layer: Censorship at the network layer involves blocking or filtering specific IP addresses or domain names. This can occur through techniques such as routing traffic away from targeted destinations or employing firewalls to restrict access to particular addresses.
-
Transport Layer: Throttling, the intentional slowing down of internet speeds for certain activities or services, typically occurs at the transport layer. By manipulating data packet transmission, authorities can impede access to specific content types.
-
Application Layer: Censorship at the application layer is often carried out by governments or ISPs targeting specific applications or protocols. For instance, in some countries, messaging apps like WhatsApp or Telegram may be blocked or restricted to control the flow of information and suppress dissent.
In summary, censorship can occur at various levels of the internet protocol stack, from physical disruptions to targeted content filtering. Any disruption along the network chain can hinder access to internet services, a convenience often taken for granted.
** 3.3 Mitigation strategies:**
In the face of increasing censorship practices across various layers of the internet protocol stack, it becomes imperative to explore strategies to safeguard digital freedoms and ensure unimpeded access to information. This section delves into potential solutions and mitigation techniques to counteract censorship efforts, ranging from technological innovations to policy advocacy.
One thing these cryptographic techniques won’t prevent is exposing your IP address (sender) as well at the IP address of the resource you are requesting (receiver). There are also a few tools that you can use to remedy this and try to hide your tracks, such as a VPN or TOR.
3.3.1 VPN
A Virtual Private Network (VPN) provides strong encryption protections to secure your Wi-Fi network. Normally, your web traffic is sent through your Internet Service Provider (ISP). But with a VPN, your traffic is first routed and encrypted through a VPN server. That means that your data and communications appear to come from the VPN server rather than your router. In other words, not only is your data encrypted, but all your communications appear to originate from the VPN server, which increases your privacy. If you use Wi-Fi security protocols, you may be wondering why you need a VPN. VPNs increase the standard protection provided by normal Wi-Fi security protocols. Because all your web traffic is diverted to a VPN server, your activity stays hidden from your ISP, government, hackers, and other snoops. Also, a VPN lets you safely browse on public Wi-Fi, and it helps you avoid geo-blocks so you can access your favourite content online. Wi-Fi security protocols and VPNs can work together to keep you safe online. Wi-Fi security protocols like WPA2 protect your local network from intrusions and breaches, while VPNs encrypt all your outgoing web traffic.
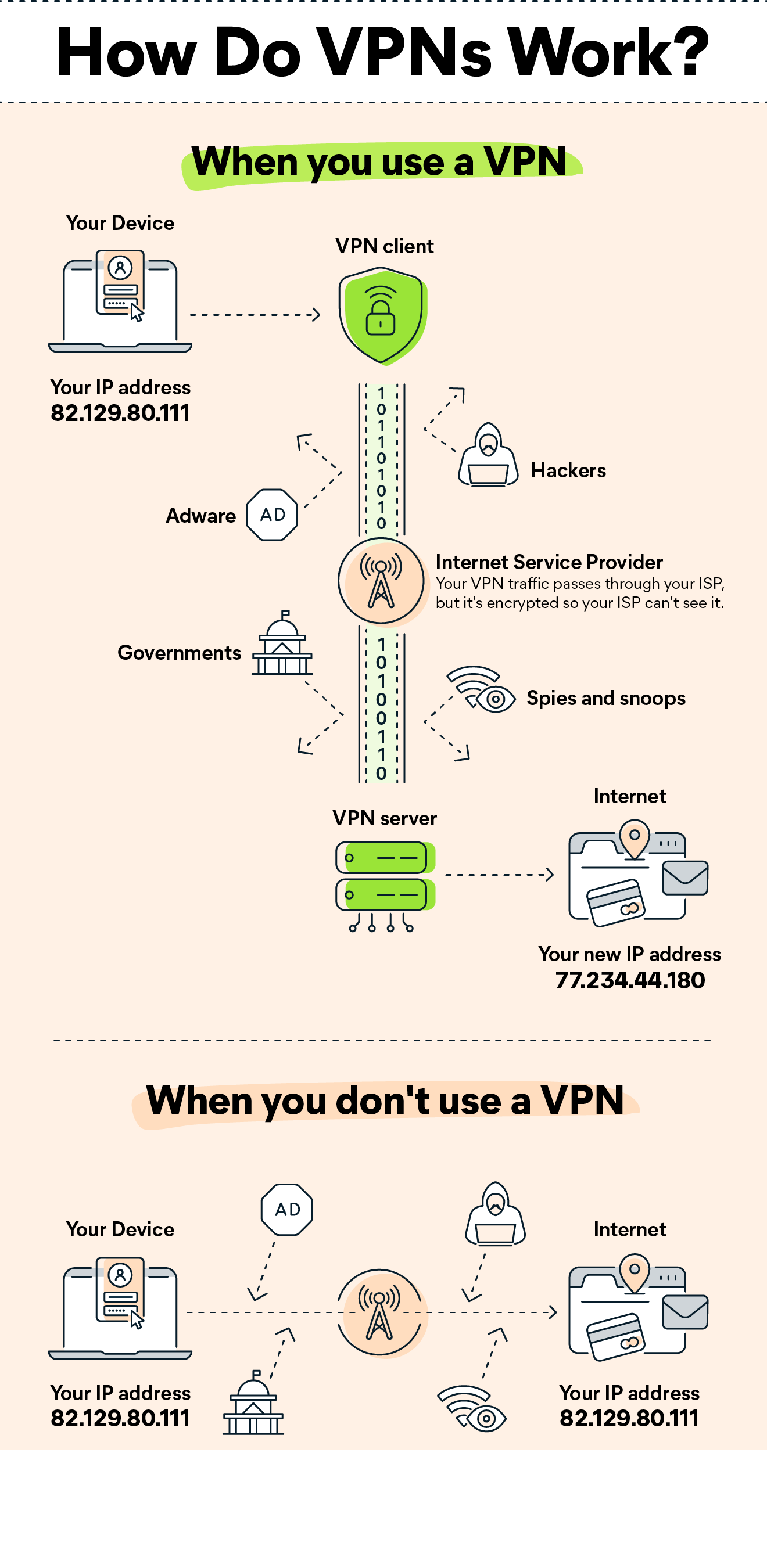
Staying safe on the internet is thus a collection of measures that need to be taken at different levels.
One easy way to stay safe on public Wi-Fi is to use one of the best privacy browsers, and to follow a few basic safety tips like verifying the security of your network, not divulging your personal info while connected The best browser for protecting your privacy is a dedicated secure browser like Brave or TOR among others. These private browsers offer significantly stronger built-in security and privacy features than popular web browsers like Google Chrome or Microsoft Edge. TOR is unlike any other browser and deserves a section of its own to detail its functioning and its measures to ensure privacy and security.
3.3.2 TOR
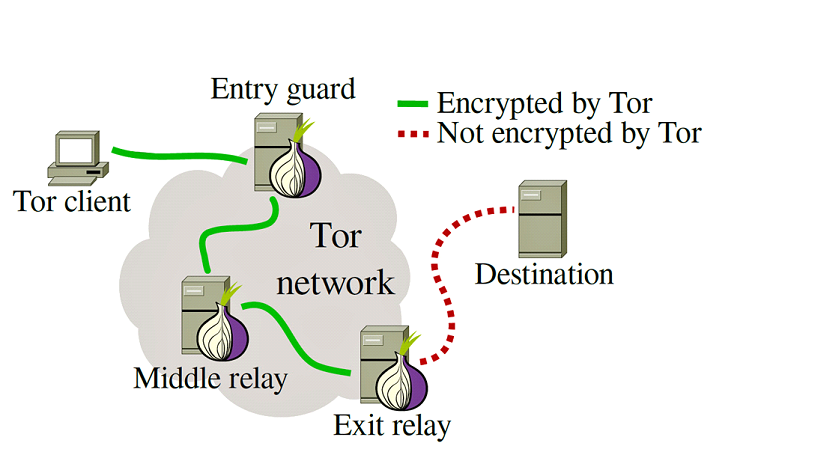
If you're looking to stay anonymous online, Tor is a network designed to help with this. Tor operates through a network of volunteers (currently around 6500 nodes) who redirect data packets from users through their network. Here's a simple way to understand how it works: instead of sending a packet directly to its destination, Tor sends a packet wrapped in three layers (that's why it's called 'The Onion Router’), with each layer containing its own address tag. The packet goes through three intermediary nodes before reaching its final destination. At each step of the way, the node unwraps a new layer containing the new destination address. Therefore, when the web server receives the request, it doesn't see it coming from your IP address but from the last intermediary, often referred to as the exit relay or node. This layered approach helps in keeping your online activities more private and anonymous.
3.3.3 Decentralised Internet
As a blockchain enthusiast, I appreciate decentralised solutions that can bolster internet resilience. The Helium network, with its decentralised network of hotspots, offers a promising approach. It utilises the WHIP protocol for communication through radio frequencies, establishing an alternative pathway to traditional internet infrastructure. This permissionless network allows anyone to contribute by deploying hotspots and routers, facilitating internet access. Leveraging the Solana blockchain, these hotspots act as miners, validating transactions and earning rewards. Importantly, the network incentivises optimal coverage in underserved areas, promoting wider internet access, while discouraging redundancy in well-served regions. While not directly designed for bypassing censorship, Helium's decentralised nature offers resilience. If one area experiences internet shutdowns, other hotspots can maintain connectivity. Additionally, the blockchain-based transparency makes it harder for entities to manipulate the network for censorship purposes. While Helium doesn't directly enhance privacy, its decentralised approach and transparency offer potential indirect benefits. It reduces reliance on single ISPs, potentially weakening their control over data flow. Moreover, the blockchain's transparency allows users to understand data routing and storage, fostering trust and deterring potential misuse. It's crucial to remember that Helium has limitations, such as its reliance on existing infrastructure for connection and potential regulatory hurdles. However, user awareness and education about Helium and other decentralised solutions can empower individuals to build a more resilient and potentially more privacy-conscious internet landscape.
Summary
Our exploration of the digital realm has unveiled a tapestry of technologies, protocols, and values that shape our online experiences. From the intricate and harmonious dance of data packets traversing networks to the profound implications of privacy and censorship, we've delved into the complexities that define our digital era. At the core of this journey lies the imperative to safeguard our digital interactions, balancing the imperatives of connectivity with the imperatives of security and freedom. Through the lens of cryptography, we've glimpsed the mechanisms by which we authenticate messages and secure our communications, forging trust in an environment fraught with potential threats. Yet, as we endeavour to protect our digital footprints, we confront the pervasive spectre of censorship, manifesting at every layer of the internet protocol stack. In response to these challenges, we've explored an array of mitigation strategies and decentralised solutions. From the anonymity offered by TOR to the encryption fortifications of Virtual Private Networks (VPNs), we've harnessed technological innovations to preserve our digital freedoms and circumvent censorship efforts. Moreover, initiatives like the Helium network offer a decentralised paradigm that not only enhances internet resilience but also fosters transparency and trust in data governance. As stewards of the digital frontier, our choices today resonate far beyond the confines of cyberspace, shaping the contours of our collective digital destiny. By embracing a holistic approach that integrates technological innovation with policy advocacy and user education, we can chart a course towards an internet that remains open, inclusive, and secure for generations to come. In this vast and ever-evolving landscape, our navigation is guided by the principles of connectivity, privacy, and freedom, ensuring that the digital frontier remains a realm of boundless possibility and enduring integrity.




评论 (0)