While developing the Ethereum Distribution System (EDS) in Peeramid Labs, we embarked on formalizing certain design aspects with the introduction of ERC-7744. During the security analysis of ERC-7744, we identified a potential compatibility issue with EIP-7702. Upon further investigation, we discovered that this issue was an ecosystem-wide concern, affecting any project that relies on the code hash of deployed bytecode (checks `EXTCODEHASH` value).
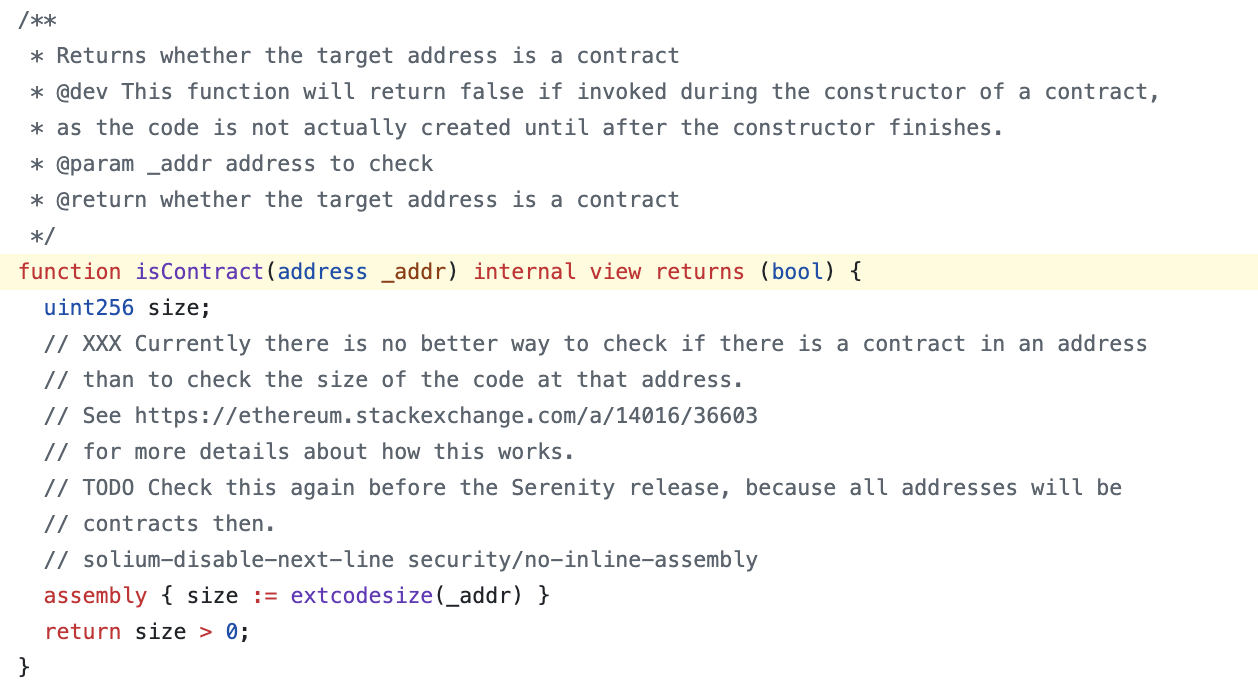
Among the identified projects were a large ecosystem of contracts that rely on the isContract function implementation of OpenZeppelin libraries to validate that an account cannot have code (i.e., fallback functions) and numerous other implementations that depend on the EXTCODEHASH opcode in their code.
The disclosure of this vulnerability was made on the Ethereum Magicians forum. After discussion, the issue was addressed and fixed by Frangio in a pull request to the EIPs repository.
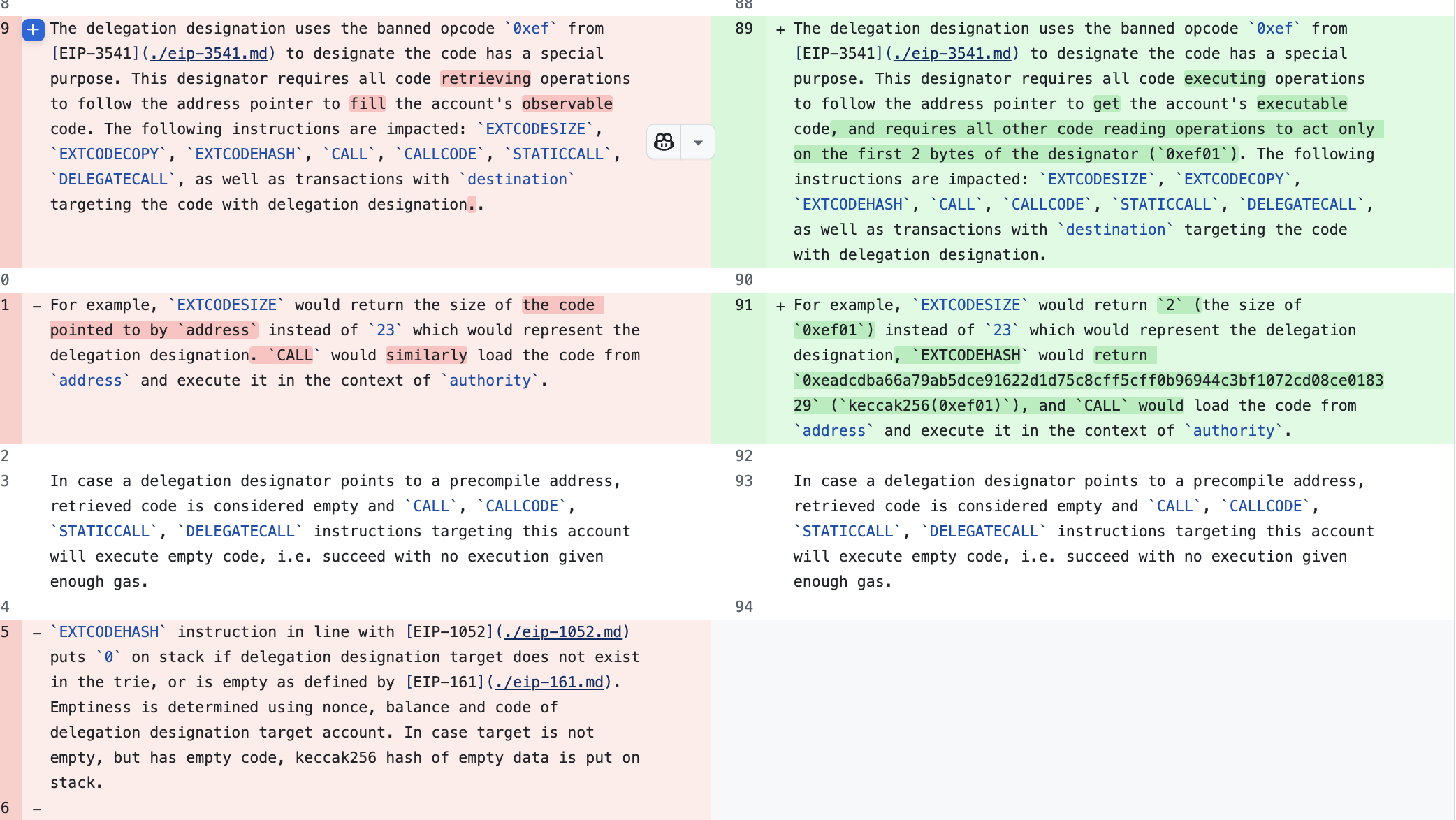
This vulnerability was discovered while EIP-7702 was already in the "Review" stage, a critical phase for community and expert scrutiny. This highlights a crucial gap in the EIP process: despite the "Review" stage, incentives for in-depth security analysis are lacking.
While early problem identification is essential, developers often focus on their own project needs. Neither EDS development nor our review of EIP-7702 were driven by direct incentives. This raises a critical question: how can we better incentivize the vital security analysis that Ethereum standards require?
We believe retroactive funding for such contributions would be a powerful acknowledgment of their value to the ecosystem. This would encourage more proactive participation in the EIP process, ultimately leading to more robust and secure standards for everyone.



评论 (0)