"If Ethereum contracts were people, proxies would be those friends who always say 'let me introduce you to someone who actually knows what they're talking about'"
Proxies are a fundamental design pattern in Ethereum smart contract development that enable upgradeability and flexibility. Let's dive into these digital middlemen that make the "immutable" blockchain surprisingly... mutable!
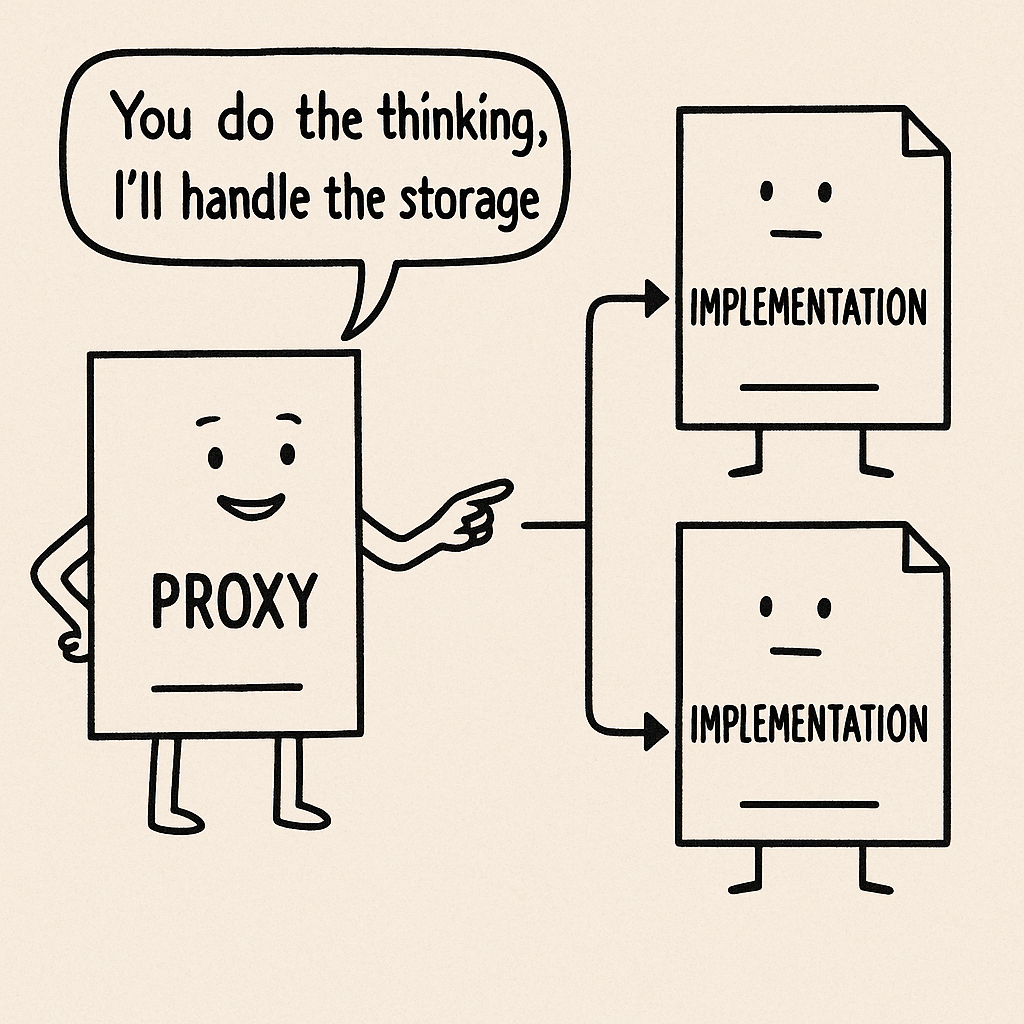
What are Proxies in Ethereum? (Or: How to Teach Old Contracts New Tricks)
Ethereum smart contracts are immutable by design - once deployed, their code cannot be changed. It's like setting your dinner choice in stone before knowing the restaurant's menu. While this immutability provides security guarantees, it creates challenges when you need to:
-
Fix bugs in deployed contracts (oops, my code had a typo!)
-
Add new features to existing applications (where's that "dark mode" button?)
-
Optimize gas consumption (because nobody likes paying more ETH than necessary)
-
Adapt to protocol changes (keeping up with the Ethereums)
"A smart contract walks into a bar. The bartender says 'We don't serve your kind here.' The contract replies, 'That's fine, I'll just deploy a proxy to order for me.'"
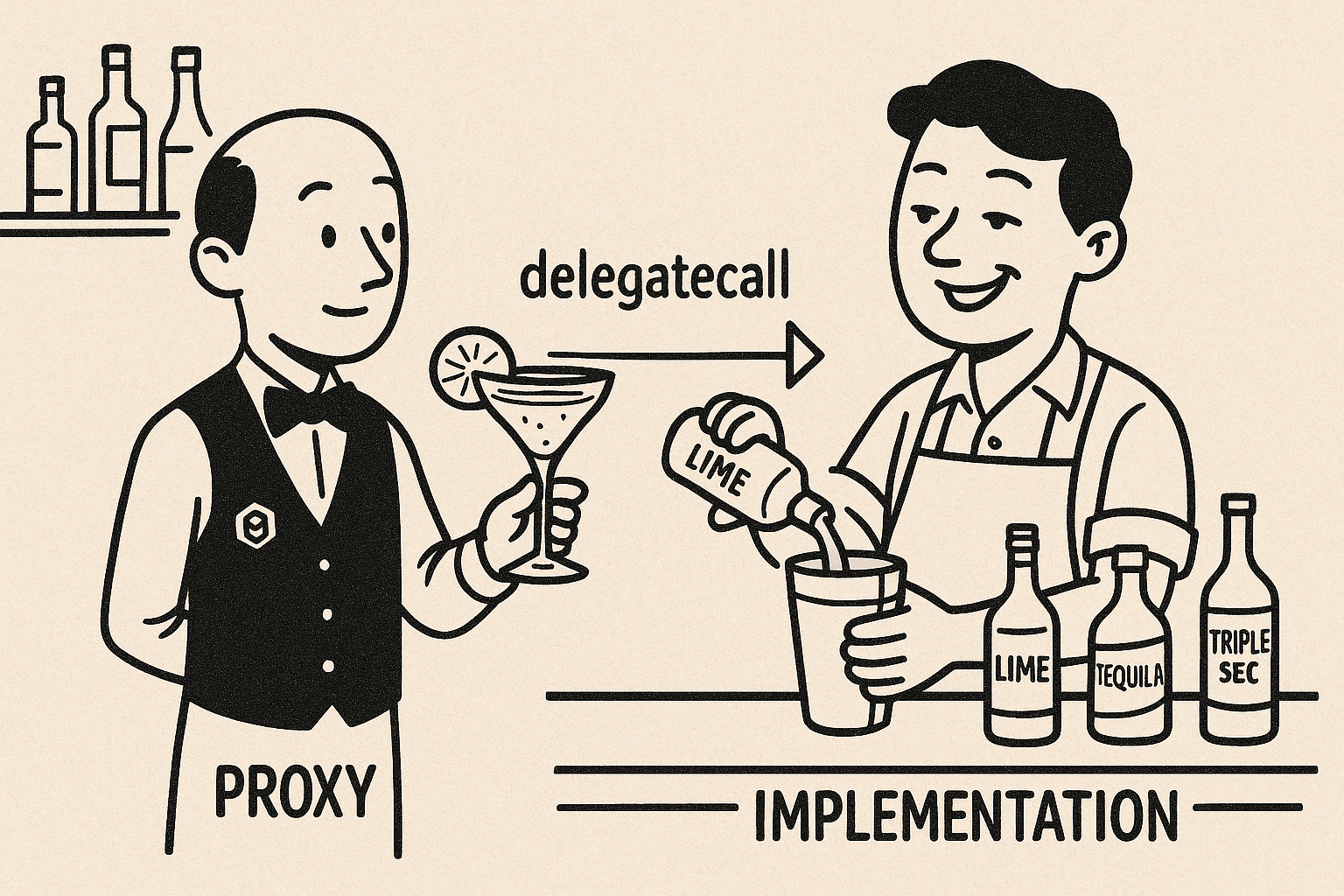
Proxies solve this problem by separating contract logic from storage and creating a forwarding mechanism:
-
Proxy Contract: Maintains the storage and state, and forwards calls to an implementation (the responsible adult in the room)
-
Implementation Contract: Contains the actual logic but doesn't store state (the replaceable brain)
-
Delegate Call: The mechanism that allows the proxy to execute logic from the implementation while maintaining its own storage context (magic!)
Core EIPs Related to Proxies (The Proxy Family Tree)
EIP-897: DelegateProxy
The Original Proxy Ancestor
This EIP standardized one of the earliest proxy patterns, establishing the concept of delegating calls to an implementation contract while maintaining state in the proxy.
"EIP-897 is like that grandparent who started a family tradition nobody fully understands but everyone follows anyway."
EIP-1822: Universal Upgradeable Proxy Standard (UUPS)
The Efficient Cousin
The UUPS pattern puts the upgrade logic in the implementation contract rather than the proxy itself. This creates a cleaner separation of concerns and can save gas costs.
Key characteristics:
-
Upgrade logic resides in the implementation (implementation says "I'll decide when I'm replaced")
-
Uses a specific storage slot for the implementation address (a special hiding place)
-
Requires implementing the
upgradeTofunction in the implementation (the self-replacement button)
"UUPS is that friend who says 'I'll tell you when I've had enough' at parties"
EIP-1967: Standard Proxy Storage Slots
The Organized Sibling
This EIP standardizes specific storage slots for proxy-related variables to prevent storage collisions between the proxy and implementation contracts:
// Implementation address: keccak256("eip1967.proxy.implementation") - 1
bytes32 internal constant _IMPLEMENTATION_SLOT = 0x360894a13ba1a3210667c828492db98dca3e2076cc3735a920a3ca505d382bbc;
// Admin address: keccak256("eip1967.proxy.admin") - 1
bytes32 internal constant _ADMIN_SLOT = 0xb53127684a568b3173ae13b9f8a6016e243e63b6e8ee1178d6a717850b5d6103;
"EIP-1967 is like labeling all your kitchen drawers so nobody puts the forks where the spoons should go."
EIP-2535: Diamond Standard
The Overachieving Youngest Child
The Diamond pattern takes proxies to the next level, allowing multiple implementation contracts (facets) to be used by a single proxy:
-
Allows partial upgrades of specific functions (replacing just the broken parts)
-
Enables modular design with specialized facets (different tools for different jobs)
-
Overcomes contract size limitations (because size does matter in blockchain)
"If regular proxies are like changing the engine in your car, Diamond proxies are like swapping out individual spark plugs while driving."

Best Practices for Using Proxies (Or: How Not to Shoot Yourself in the Foot)
-
Always initialize implementation contracts to prevent attackers from taking control (lock your doors!)
-
Use transparent proxy patterns to avoid function selector clashes (no name tag confusion)
-
Consider storage layout carefully when upgrading contracts (don't put new furniture on top of old pets)
-
Implement access controls for upgrade functionality (not everyone should have the launch codes)
-
Verify implementation contracts before upgrading (look before you leap)
"How many Ethereum developers does it take to upgrade a proxy contract? One to write the code and five to argue about which proxy pattern to use."
Challenges and Considerations (The Fine Print)
-
Storage collisions: Different implementations might use the same storage slots differently (two people writing on the same whiteboard)
-
Function selector clashes: Function names in proxy might clash with implementations (when your new friend has the same name as your proxy)
-
Security risks: Bugs in upgrade mechanisms can lead to permanent loss of funds (the "oops" that costs millions)
-
Gas costs: Proxies add overhead to each transaction (nothing in life is free, especially on Ethereum)

Conclusion
Proxies have become an essential part of Ethereum development, enabling upgradeable and adaptable smart contracts. Understanding the relevant EIPs is crucial for implementing them correctly and securely. As the ecosystem evolves, proxy patterns continue to mature, offering more sophisticated solutions to the immutability challenges of blockchain development.
"A proxy contract and an implementation contract walk into a bar. The bartender asks, 'What can I get you?' The proxy turns to the implementation and says, 'You handle this’"
Keywords: Ethereum proxy contracts, smart contract upgradeability, EIP-1967, EIP-2535, Diamond proxy, UUPS proxy, delegate calls, blockchain upgrades, immutable contracts, Ethereum development patterns, solidity proxy pattern, transparent proxy



评论 (0)